If you’ve ever wondered what an email bombing attack is and how it affects email security, here’s a clear explanation. An email bomb refers to a malicious cyber attack where a victim’s inbox or mail server is flooded with an overwhelming number of emails, often in the hundreds or thousands, within a short period.
This surge of messages can severely disrupt email services, leading to issues such as unresponsive mail servers or obstructing legitimate communication. Email bombing is a type of denial of service (DoS) attack targeting the email system, often creating chaos to mask more dangerous activities like fraudulent transactions or unauthorized access. Sometimes, attackers use this tactic as a distraction to conceal other malicious operations within a network.
Recognizing this threat is essential in today’s digital era, where attackers exploit email security vulnerabilities to gain initial access or carry out social engineering attacks. This article will delve into the motives behind email bombing attacks, their mechanics, and strategies to protect your email address and infrastructure from being targeted.
One way to keep your inbox 100% clean from spam or unwanted emails is by using our Cleanfox platform. It’s not only completely free, but it also helps you secure your email more effectively.
Understanding Email Bombing
Definition and Mechanics of Email Bombing
Email bombing is a type of cyberattack where a threat actor intentionally floods a victim’s email address or mail server with a massive flood of emails in a short time. This flood can consume system resources such as bandwidth, disk space, and processing capacity, effectively disrupting normal email communication and potentially leading to a denial of service (DoS) attack. The mechanics often involve the attacker leveraging botnets or exploiting subscription services to trigger a cascade of confirmation emails or newsletters.

Emails from varied senders, domains, and languages often bypass spam filters that detect repetitive content. For instance, attackers frequently exploit legitimate marketing platforms like Mailchimp to send thousands of seemingly legitimate subscription confirmation emails to the victim. This makes it challenging for email security tools to flag the activity as malicious.
The real threat lies in the sheer volume of messages. This overwhelming stream can obscure critical alerts, essential transaction confirmations, and other vital communications, effectively masking the threat actor’s other activities on the victim’s network or remote systems.
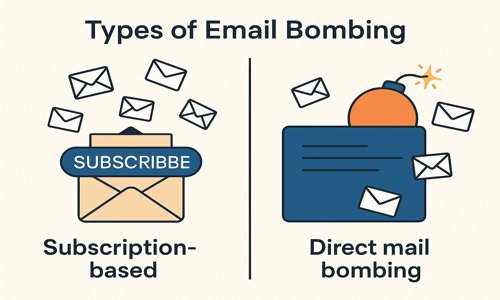
Types of Email Bombing Attacks
There are several types of email bombing attacks, but two common categories stand out:
- Subscription-based Attacks: In this scenario, attackers sign a victim’s email address up for numerous newsletters and services, generating a flood of confirmation emails. These messages typically bypass spam filters because they are transactional and appear legitimate. However, the sheer volume creates a cluttered inbox, serving as a smokescreen to conceal serious threats such as fraud confirmation emails or a Black Basta ransomware negotiation email.
- Direct Mail Bombing: Here, attackers send millions of spam or malicious emails directly to the victim’s server, often using compromised systems within a botnet. This can lead to server downtime, disrupt business operations, and potentially expose systems to additional social engineering attacks.
Both types of attacks aim to deny service and overwhelm managed detection response (MDR) services and security teams. Delaying or preventing timely incident response. When combined with other tactics like remote desktop protocol exploitation or command control web access, email bombing becomes a highly effective weapon in a threat actor’s arsenal.
Why Email Bombing Occurs
Email Bombing as a Distractive Tool
One of the primary reasons threat actors engage in email bombing attacks is to create a distraction. By flooding a victim’s inbox with hundreds or thousands of unwanted emails, attackers aim to mask other more dangerous activities happening behind the scenes.
These may include fraudulent transactions, data exfiltration, or lateral movement within a compromised network. For instance, if a cybercriminal initiates a fraudulent financial transaction linked to your account, they could use a subscription-based email bombing attack to overwhelm your inbox with confirmation emails from multiple services. This overload can bury critical alerts and confirmations, making it difficult for you or your security team to detect the attack in time or respond effectively.

Such a tactic effectively hampers your incident response and allows the attacker to operate under the radar while your focus is on managing what appears to be a flood of spam or legitimate-looking alerts.
Email Bombing as a Tool for Revenge or Blackmail
Aside from acting as a smokescreen, email bombing is also often used as a tool of revenge or blackmail by malicious actors. When motivated by personal vendettas or attempts at coercion, attackers flood the victim’s email address with an overwhelming volume of messages to disrupt daily communication and cause significant distress.

This can cripple communication channels, leading to lost business opportunities or inability to access vital information. In organizational contexts, such mail bombing attacks may be part of a broader campaign, sometimes combined with other threats like ransomware (such as Black Basta ransomware) or social engineering ploys to pressure the victim into paying a ransom or meeting demands. This tactic exploits the victim’s dependence on uninterrupted email service and the disruption caused by the denial of service (DoS) attack on their mail server to amplify the impact of the threat.
Preventive Measures and Mitigation Strategies
Strengthening Email Filters
One of the most effective ways to protect yourself from email bombing attacks is by enhancing your email security filters. Modern filtering systems use advanced machine learning and heuristic analysis to categorize incoming emails into spam, bulk mail, or potentially malicious categories such as phishing or malware.
Say goodbye to spam, clutter, and chaos.
Our smart email cleaner filters out junk, organizes your inbox, and helps you focus on what really matters.
✅ Block spam automatically
✅ Organize emails by priority
✅ Keep your inbox clean
✅ Clean old emails you don’t read
📱 Available on the App Store and Google Play.
These filters can automatically quarantine suspicious messages, reducing the risk of harmful or excessive emails reaching your inbox. Additionally, employing protocols like DMARC, SPF, and DKIM helps authenticate incoming emails, preventing spoofing attempts commonly used during mail bombing attacks. If you manage your own email server, configure it to block or rate-limit emails from suspicious or unknown senders to minimize your attack surface. And for personal inboxes, you can also learn how to block an email on Yahoo Mail easily to stop unwanted senders directly.
Implementing Rate Limiting and CAPTCHA
To mitigate the impact of subscription-based email bombing, deploying rate limiting on your mail server or application endpoints can significantly slow down or prevent flood attacks. This technique limits emails or requests from a specific IP or source within a defined time frame.
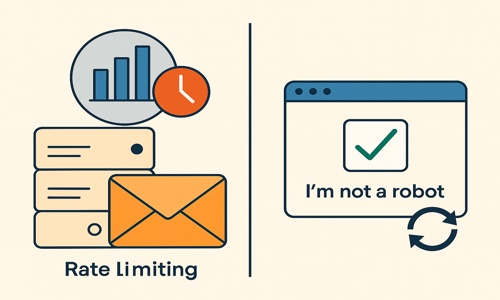
Another effective tool is the implementation of CAPTCHA on signup forms and unsolicited email requests. This helps verify that incoming subscription requests are from legitimate human users. It also prevents automated bots controlled by a threat actor. Rate limiting and CAPTCHA form layered protection against unwanted subscription confirmation emails.
Regular System Monitoring and Alerts
Constant vigilance is essential for early detection and effective response to an email bomb attack. Use email monitoring tools to detect spikes in activity or unusual volumes of confirmation emails.

Setting up real-time alerts for these anomalies enables your security or managed detection response (MDR) teams to investigate and react swiftly before the attack escalates into a system-wide denial of service (DoS) attack. In regulated industries, detailed logging and documentation of these events can also support compliance requirements during audits or incident investigations. Training your team to spot early signs of email bombing builds a strong human firewall against attacks
Conclusion 💡
Email bombing exploits trusted services to overwhelm inboxes and distract from more malicious cyber activities. To protect yourself, focus on strengthening email filters, implementing rate limiting, and closely monitoring your inbox for unusual patterns.
Services like Darktrace and Tencent Cloud offer robust solutions to mitigate these threats. Understanding tactics and acting early helps protect your email and prevent attackers from exploiting email bombing.
Stay vigilant and take action today to secure your digital communications.
FAQ 📘❓
What are the common methods attackers use to carry out email bombing?
Common email bombing methods include:
- Mass mailing: Sending large volumes of identical or varied emails to overwhelm inboxes, often using botnets.
- List linking (or list bombing): Subscribing the target to numerous mailing lists, causing floods of subscription emails.
- ZIP bombing: Sending compressed archives that overload server resources once decompressed.
- Attachment bombing: Sending emails with large or numerous attachments to consume storage.
- Email loops: Exploiting auto-responder misconfigurations to create endless reply chains.
- Reply-all storms: Triggering cascades of automated replies by replying to large distribution lists.
How can I identify if my inbox is currently being targeted by an email bombing attack?
To identify if your inbox is being targeted by an email bombing attack, watch for:
- A sudden flood of hundreds or thousands of emails arriving within minutes, often from multiple domains.
- Emails that include subscription confirmations, newsletters, or duplicate messages, making it hard to locate important emails.
- Slow or crashed email servers, which may indicate your inbox is under attack.
What steps can I take immediately to protect my email account and stop an ongoing email bombing attack?
To protect your email account during an email bombing attack:
- Change your password to a strong and unique one.
- Enable two-factor authentication (2FA) to block unauthorized access.
- Review and remove suspicious devices and logins from your account.
- Check email forwarding and other settings for unauthorized changes.
- Warn your contacts about potential malicious emails that may have been sent from your account.
Is it safe to click unsubscribe links on the flood of emails during an email bombing incident?
Clicking unsubscribe links during an email bombing incident is generally unsafe. These links may confirm your email is active, leading to more spam, phishing attacks, or malware exposure. Instead:
- Use your email client’s built-in unsubscribe feature (list-unsubscribe headers).
- Mark suspicious emails as spam to minimize risks.
If you liked this article and want to learn more about Email Security, check out our post: “How to Secure an Email in Outlook (Step-by-Step for 2025)” . You can also explore our blog for more helpful content.